This is the final part for building a custom firewall with the utilization of IP Reputation within Suricata.
The first step to take is to go into ‘suricata.yaml’, go to the IP Reputation section, and remove the comment tags from the configurations. The next step is to create the necessary files and directory that are listed. So make the ‘iprep’ directory and make ‘categories.txt’ and ‘reputation.list’ inside of the directory.
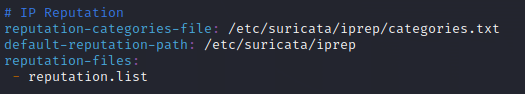
For formatting these two files properly, here are screenshots from the Suricata documentation:
For this example, here is the ‘categories.txt’ file:
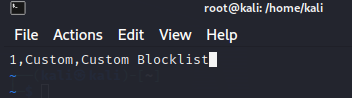
And here is the ‘reputation.list’ file:
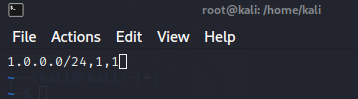
This example reputation will trigger on any IP address in the 1.0.0.0/24 range.
Now we need to go to the ‘custom.rules’ file we made with the custom Suricata alert rules and add a new rule using IP Rep.
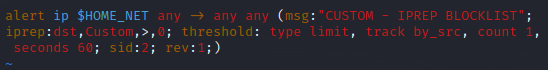
This rule alerts on IP activity from the home network going to any IP address.
iprep:dst,Custom,>,0;For the ‘iprep’ section of the rule, we are using destination, not source, to prevent blocking our internal IP address. ‘Custom’ is the category name from the ‘categories.txt’ file. The ‘>,0’ indicates that anything with a reputation greater than 0 will be detected and blocked. This allows the potential to block thousands of IP addresses without having to make thousands of rules in the firewall.
Now to put everything together, first we will check firewall with ‘iptables’:
Currently nothing being blocked.
Next, we will make sure Supervisor is running with our alert daemon:
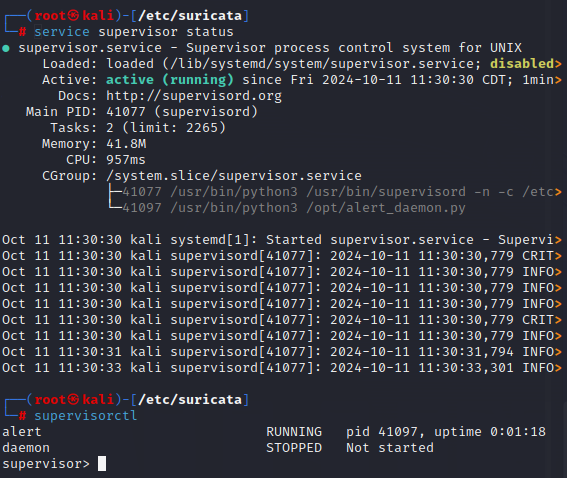
This shows the alert daemon is running.
Now we can start Suricata, then ping any address in the 1.0.0.0/24 range:
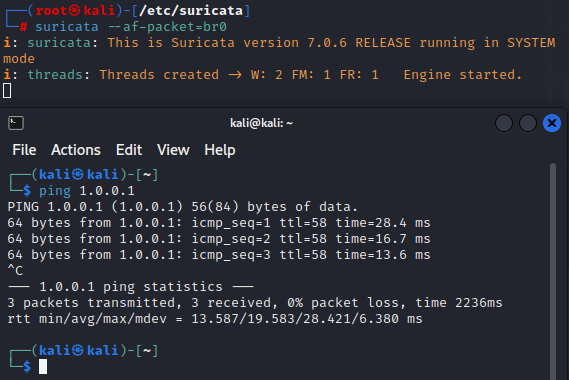
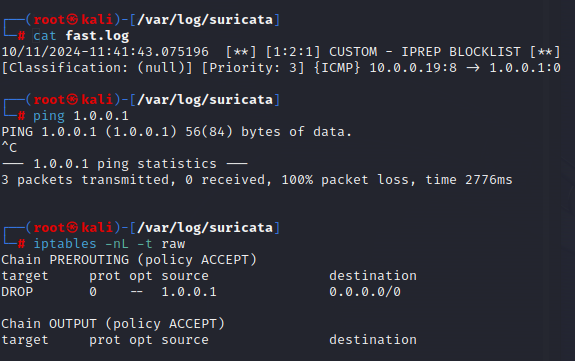
We can see that the alert was generated in the fast log, and if we try to ping 1.0.0.1 again, there is 100% packet loss this time. Checking the ‘iptables’ shows that 1.0.0.1 has been added to the firewall and is being blocked.