In this post, I will demonstrate analyzing packets with Wireshark to capture a password in clear text.
Before Wireshark can be used, we need to capture some packets with the ‘Tcpdump’ command and write them to a .pcap file:
$ tcpdump -i [web interface] -w [file name].pcapThe web interface can be identified with the ifconfig command.
My interface is br0. Now we can enter this into the Tcpdump command along with a file name, I will name the file pwnet.pcap:
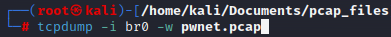
Once I start this command, Tcpdump will capture all of the packets being sent back and forth on the br0 interface. Note that the IPv4 address is 10.0.0.19.
Now that Tcpdump is running, I will open an intentionally unencrypted WordPress page and attempt to login.
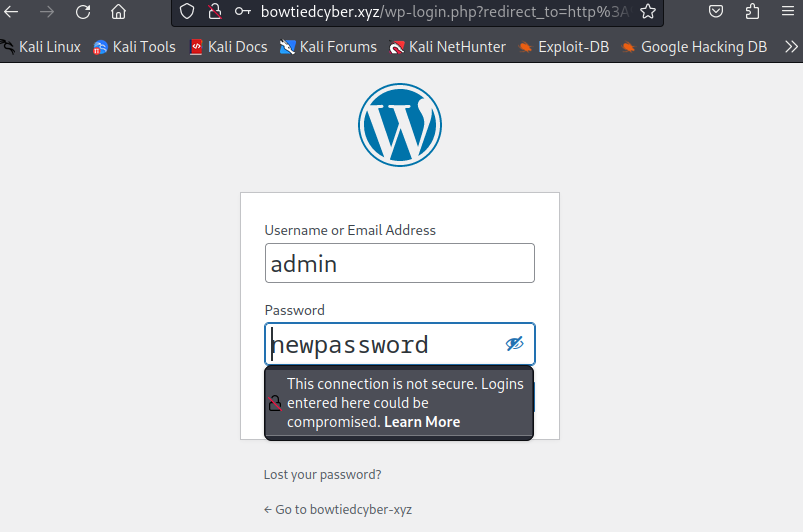
With username ‘admin’ I attempted two passwords; ‘newpassword’ and ‘oldpassword’. Both login attempts failed, but that is fine for this exercise.
We go back to the CLI and end the packet capture with ctrl+c:
Now that we have a pcap file, we can open it up in Wireshark:
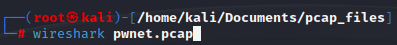
The first task is to go to the Statistics tab, IPv4 Statistics, and All Addresses
This gives us a list of IPv4 addresses that were seen and had packets captured. Two things stand out here:
- We see that two of the addresses have much higher packet counts than the rest
- One of them is my interface IP, 10.0.0.19
This means the 178.128.237.187 address is most likely associated with the unencrypted site that we tried to log into. We will start with that assumption to move forward locating the login attempt.
With this info in mind, we next go to the Statistics, Conversations tab:
Moving to the IPv4 tab we see again the number of packets between 10.0.0.19 and 178.128.237.187, bolstering our previous assumption.
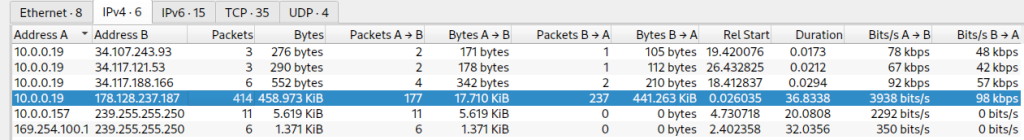
Right click on that row, Apply as Filter, Selected, and A<->B. This will filter communication both ways between these addresses.
Here are the filtered packets:
There are still a lot of packets to have to manually look through, so we can filter further by entering into the search bar [tcp contains “login”] to see if that will help narrow down the search.
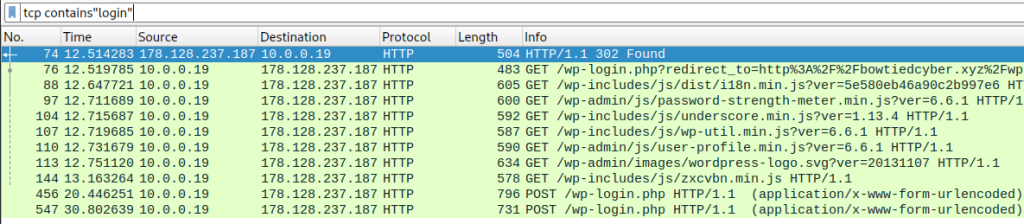
Only a handful of packets to look through now. Instead of looking at every packet, I notice that the two packets at the bottom are the only packets with POST in the info column. This could correspond with the two login attempts I made, so I will start with the first of those.
Right click that row, Follow, TCP Stream.
Now we have a readable text output.
After looking through for a bit, we can see the last red text line has the following:
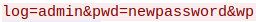
We have found the login attempt. ‘admin’ is the same username, and ‘newpassword’ was the first password I tried.