This post will demonstrate creating a custom rule in Suricata to generate an alert.
In the /etc/suricata/rules directory I made a new rules file called custom.rules:
For Suricata to run this rule, the new rule file needs to be added to the suricata.yaml file:
Now for the actual rule in the custom file:
All this rule is doing is letting us know if any TCP traffic is identified from our internal network going to 1.1.1.1, either HTTP or HTTPS.
To start Suricata, we run the --af-packet command:
Note: My interface is br0, the default is eth0.
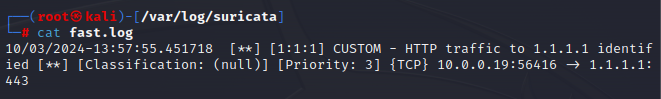
When I open a browser and go to 1.1.1.1, the alert should trigger and write to the fast.log file.
Sure enough, the alert message appears in fast.log.
This simple rule example does not do much for us by itself. However, combining it with some Python scripting and a few more functions within Linux, this becomes the first part of creating a custom firewall.